Set up single sign-on with SAML and Auth0

If you want to enable single sign-on in Timetastic, you can do so using Auth0 as your identity provider.
Note: auto-provisioning is not supported by Timetastic.
Step 1. Auth0 setup
Start by logging into your Auth0 account, head to to 'Applications' from the left hand menu, then click the '+ Create Application' button.
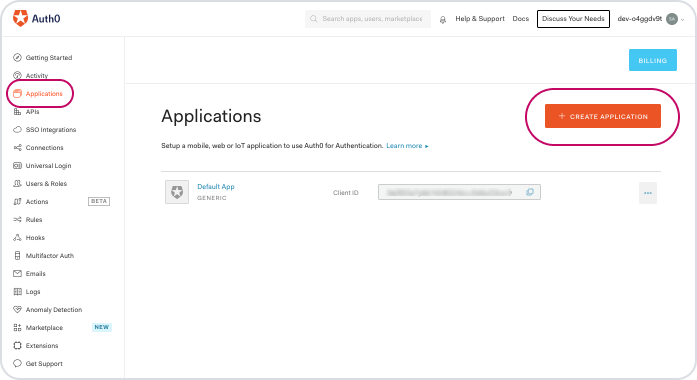
In the Name field enter 'Timetastic' then choose 'Regular Web Applications' and click 'Create'.
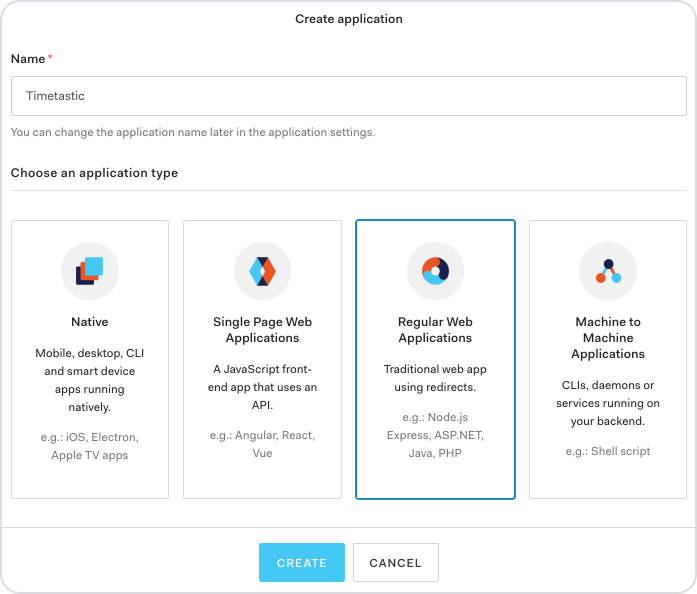
Click the 'Addons' tab.
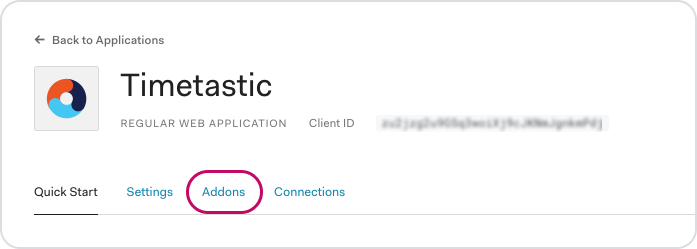
Then choose 'SAML2 Web App'.
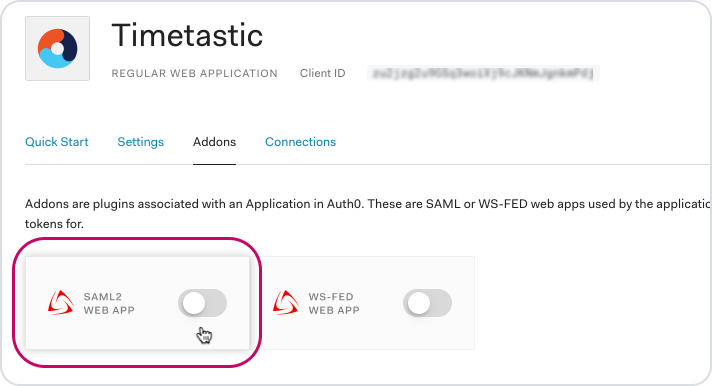
You'll now need to grab some security details from your Timetastic account.
In Timetastic, head to SETTINGS > SECURITY. Click the 'Set up SAML single sign-on' link.
Then the 'How to configure your Identity Provider' link to bring up your settings.
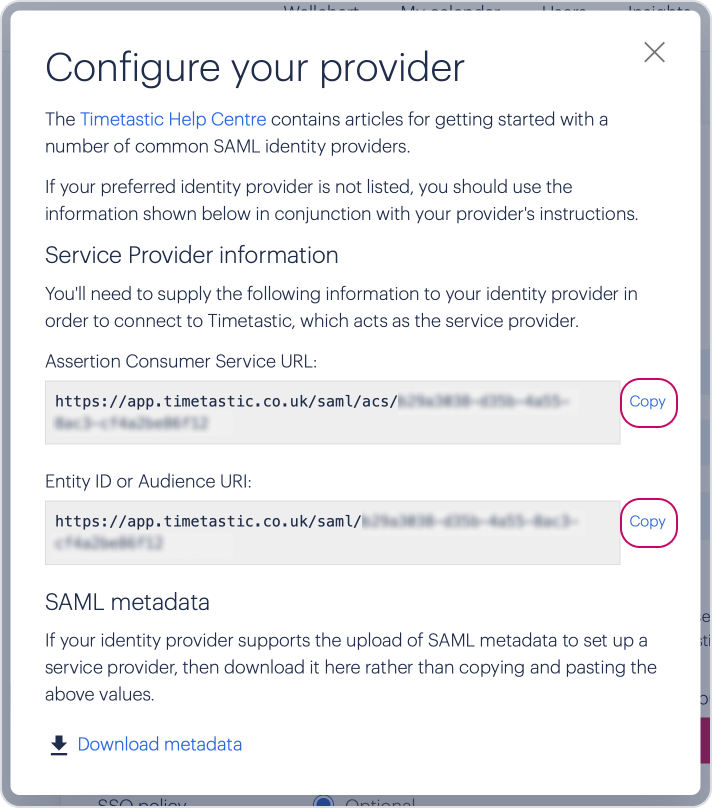
Copy the Assertion Consumer Service URL and paste it into the 'Application Callback URL' field in OneLogin.
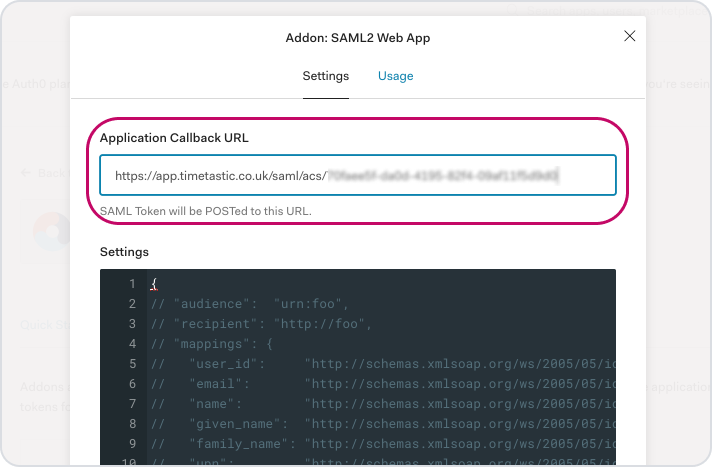
In the Settings field, replace all the existing content with the following JSON:
{
"nameIdentifierProbes": [
"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"
]
}
This tells Auth0 to identify signed-in users by their email address when passing information to Timetastic.
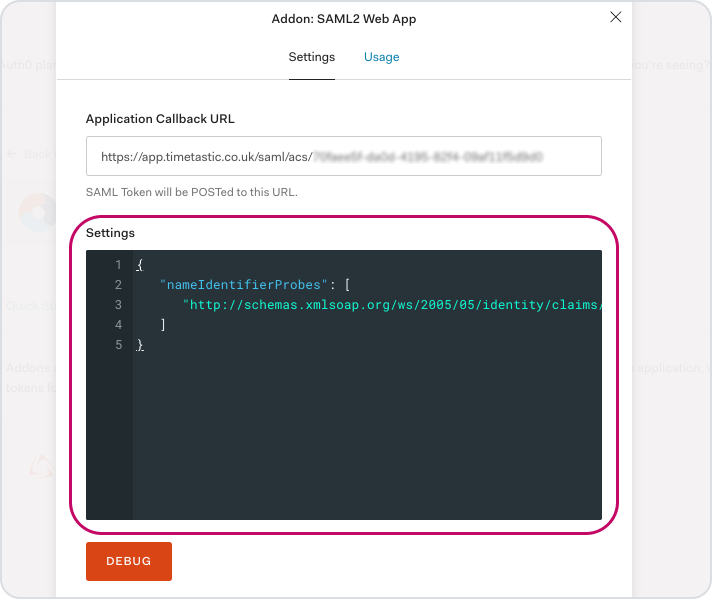
Scroll down and click 'Enable' to save your changes, then scroll back up and click on the 'Usage' Tab.
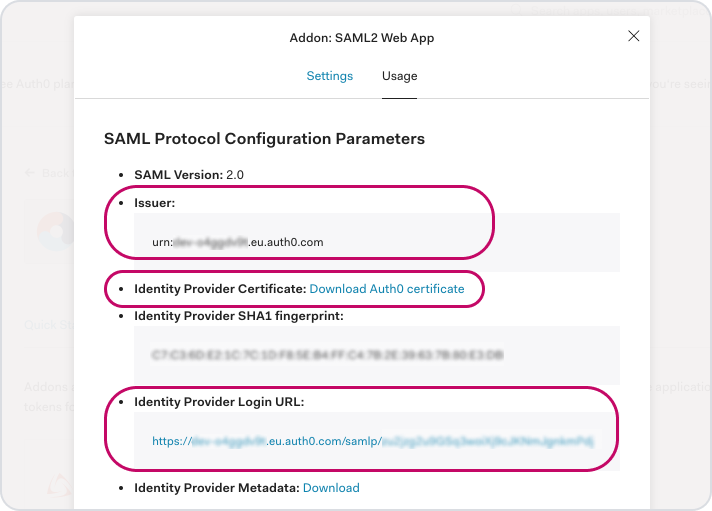
You'll need these highlighted details when setting up Timetastic.
Step 2. Timetastic setup
Now it's time to head over to Timetastic. Go back to SETTINGS > SECURITY then 'Set up SAML single sign-on'.
In the 'SAML SSO URL' field, paste the 'Identity Provider Login URL' value from the Auth0 Usage tab.
For 'Issuer entity ID', paste the 'Issuer' value from Auth0.
For 'Public certificate', click the 'Download Auth0 certificate' link.
Once you've downloaded the file, open it in a text editor and you should see the certificate value enclosed within "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----". Copy all the text and paste into the 'Public certificate' field.
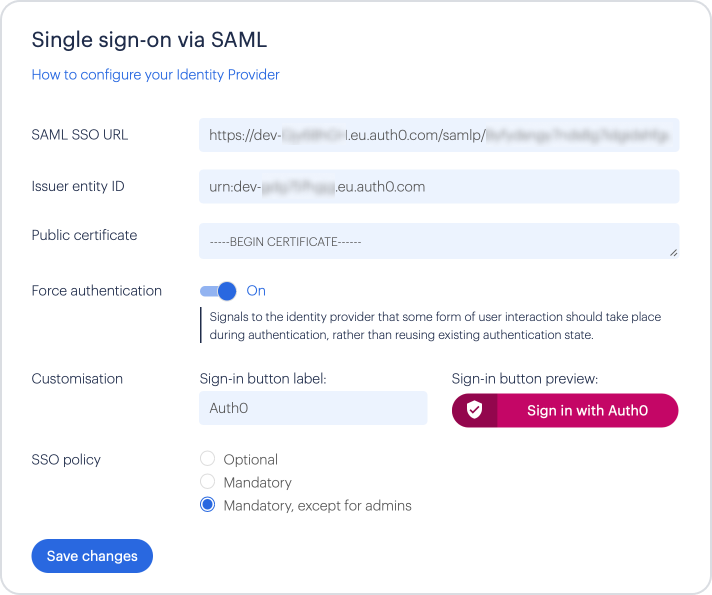
You can turn 'Force authentication' on, if you want users to have to re-enter their identity providers details. (This will only work if the identity providers also support this option)
To customise the Sign-in button, enter something useful, such as 'Auth0' against 'Customisation'.
We'd recommend you test SSO is working correctly before making it Mandatory.
Once you're happy with your settings, click 'Save Changes', then you're good to go!