Set up single sign-on with SAML and Okta

You can use single sign-on in Timetastic using Okta as your identity provider.
Note: auto-provisioning is not supported by Timetastic.
Step 1. Okta setup
Start by logging into your Okta account and head to to 'Applications' from the main menu, then click the 'Add Application' button.
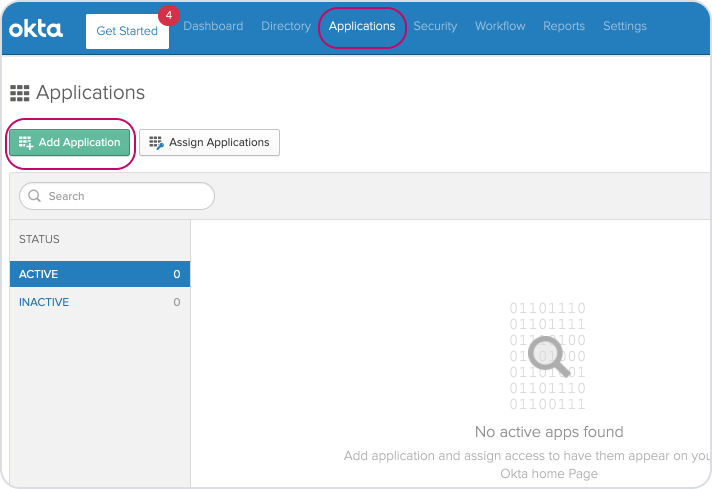
Click on the 'Create New App' button in the top right hand corner.

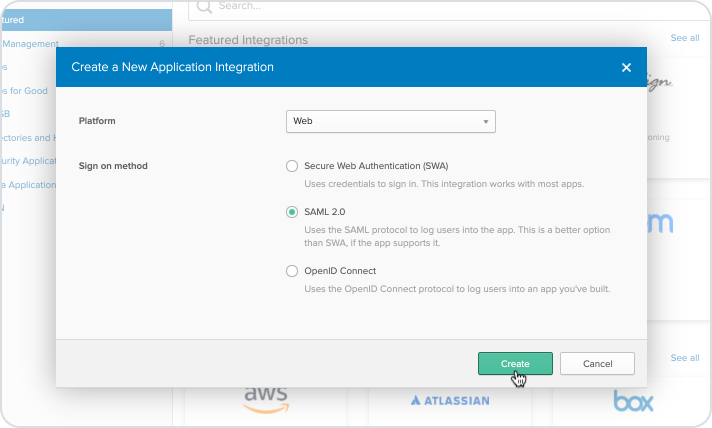
Choose Web from the 'Platform' drop down options and SAML 2.0 against the Sign on method, then click 'Create':
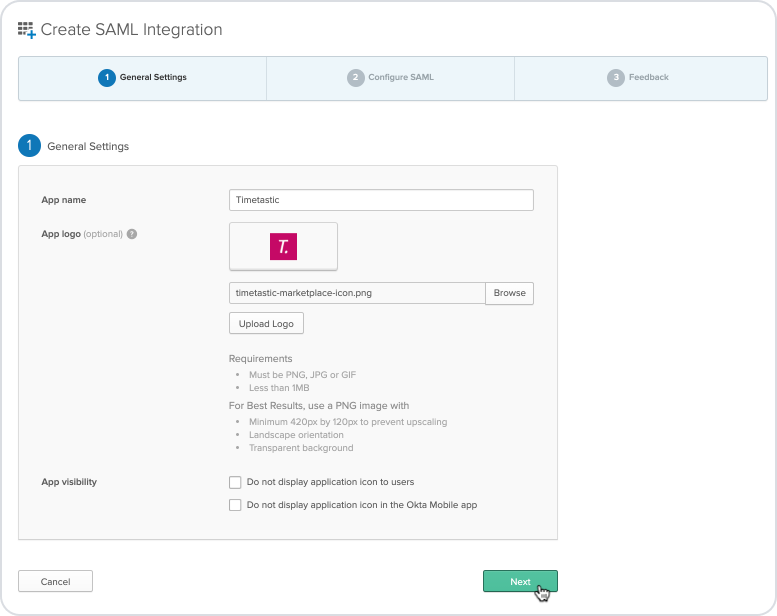
Next, under General Settings, enter a name and logo for the App to make it easy for your users to identify Timetastic within Okta, then click 'Next'.
(You can download our App icon at the very bottom of this article.)
For the next section Configure SAML, you'll need to grab some security details from your Timetastic account:
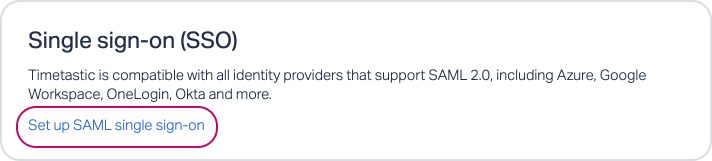
In Timetastic, head to SETTINGS > SECURITY. Click 'Set up SAML single sign-on'.
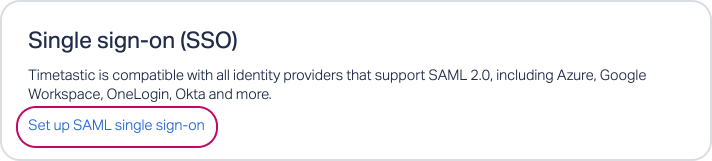
Click the 'How to configure your Identity Provider' link to bring up your settings.
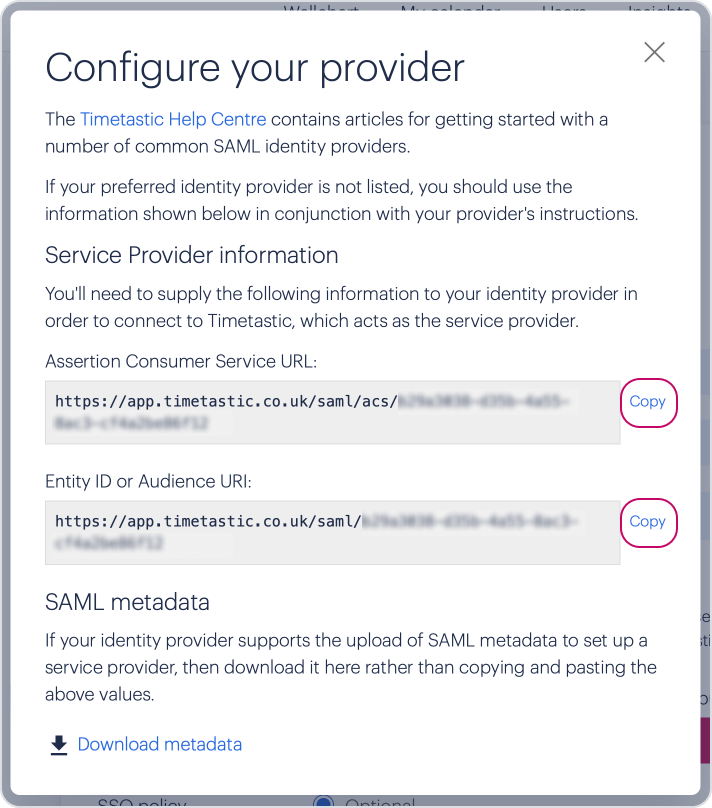
Copy the Assertion Consumer Service URL and paste it into the 'Single sign on URL' field in Okta.
Copy the Entity ID or Audience URI and paste it into the 'Audience URI (SP Entity ID)' field in Okta.
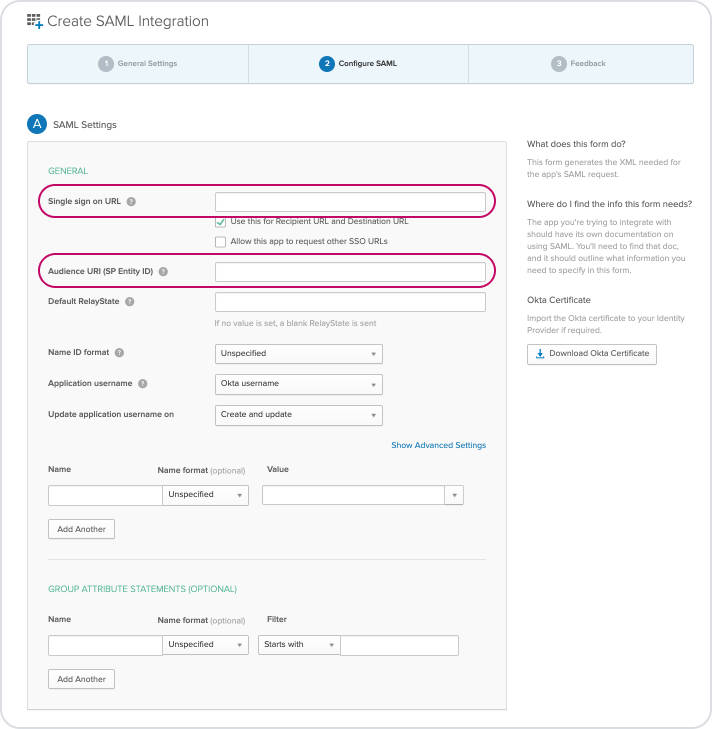
If your Okta usernames are the same as your Timetastic user email addresses, you shouldn't need to change the other default settings.
If they aren't the same, just change the drop down against 'Application username' to a field that matches your user's Timetastic email address (most likely Email).
For SSO to work, these email addresses must match the users email address registered to Timetastic.
Once you've got the settings as you need them, click 'Next'.
Under Feedback, select 'I'm an Okta customer adding an internal app', then it's up to you if you want to offer any other information. Once you're done, click 'Finish'.
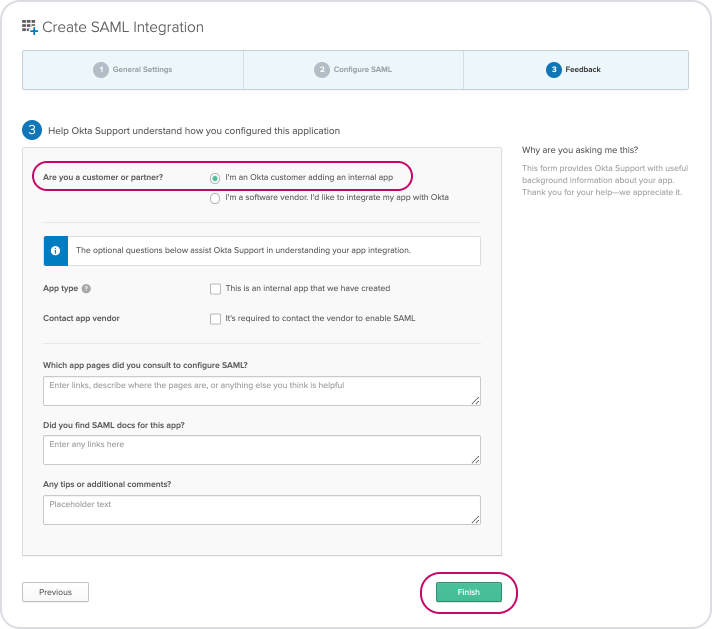
You'll now need to give people access to the app in Okta.
To assign users to the Timetastic app, click the 'Assignments' tab on the Timetastic app details page and then the 'Assign' drop down to choose either People or Groups.
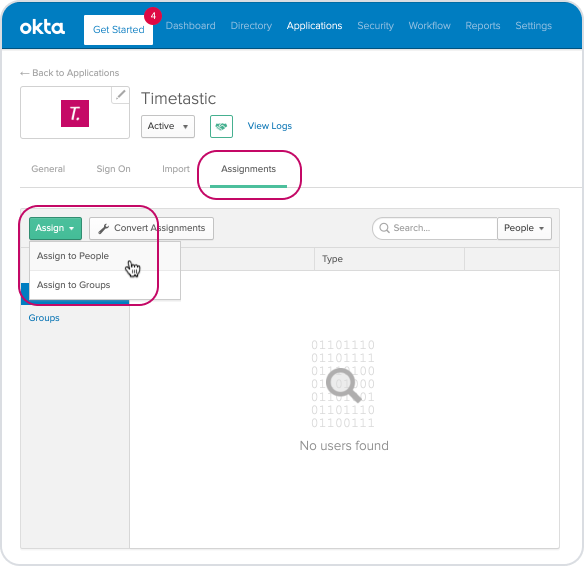
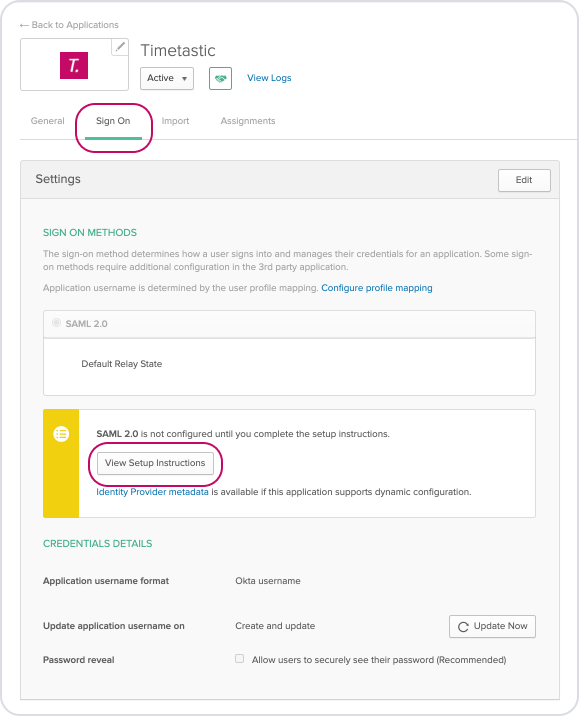
Lastly, before you leave Okta, just click the 'Sign On' tab of the app and then the 'View Setup Instructions' button.
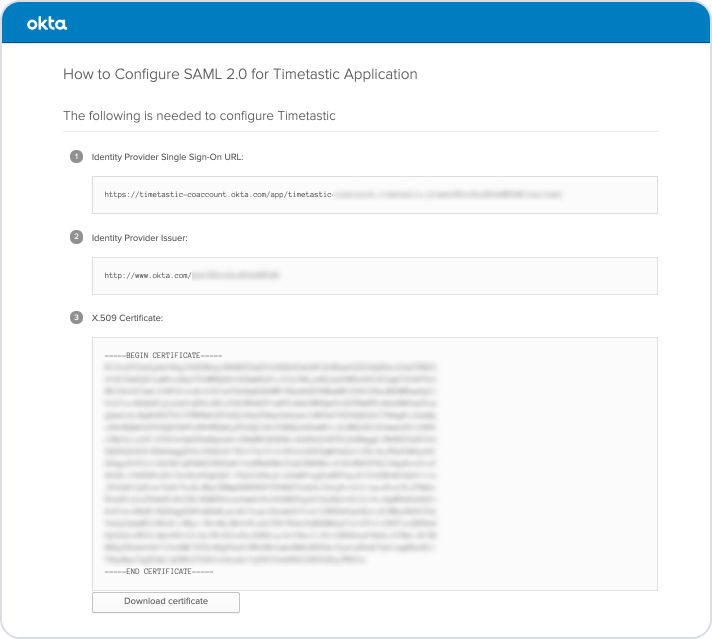
Another tab will open up in your browser with the details you'll need to enter in Timetastic.
Step 2. Timetastic setup
Now it's time to head over to Timetastic. Go back to SETTINGS > SECURITY and 'Set up SAML single sign-on'.
In the 'SAML SSO URL' field, paste the 'Identity Provider Single Sign-On URL' value from Okta.
For 'Issuer entity ID', paste the 'Identity Provider Issuer' value from Okta.
For 'Public certificate', paste the 'X.509 Certificate' value from Okta.
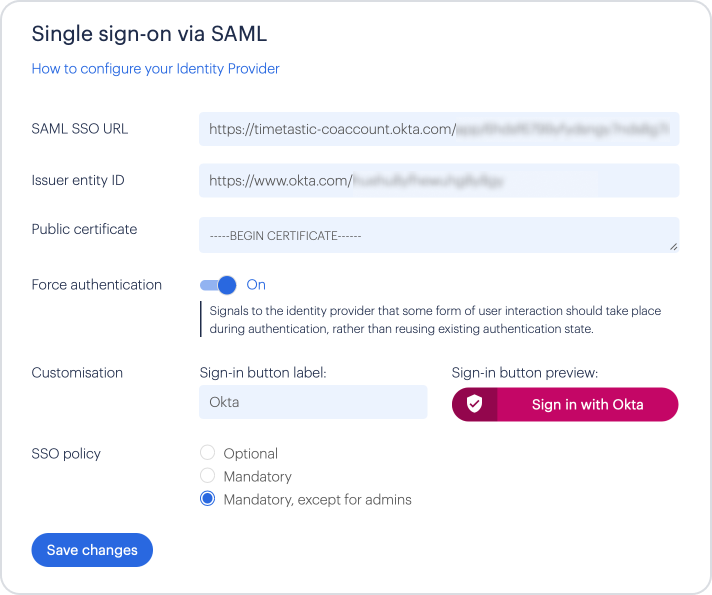
You can turn 'Force authentication' on, if you want users to have to re-enter their identity providers details. (This will only work if the identity providers also support this option)
To customise the Sign-in button, enter something useful, such as 'Okta' against 'Customisation'.
We'd recommend you test SSO is working correctly before making it mandatory.
Once you're happy with your settings, click 'Save changes', then you're good to go!
Here's the Timetastic logo to upload into Okta: