Set up single sign on with SAML and Azure AD

You can use single sign-on in Timetastic using Azure AD as your identity provider. So if you already manage users in Azure AD and Office 365 - this is for you.
Note: auto-provisioning is not supported by Timetastic.
Step 1. Azure AD setup
Start by going to 'Enterprise applications' in your Azure portal.
Click 'New application'.
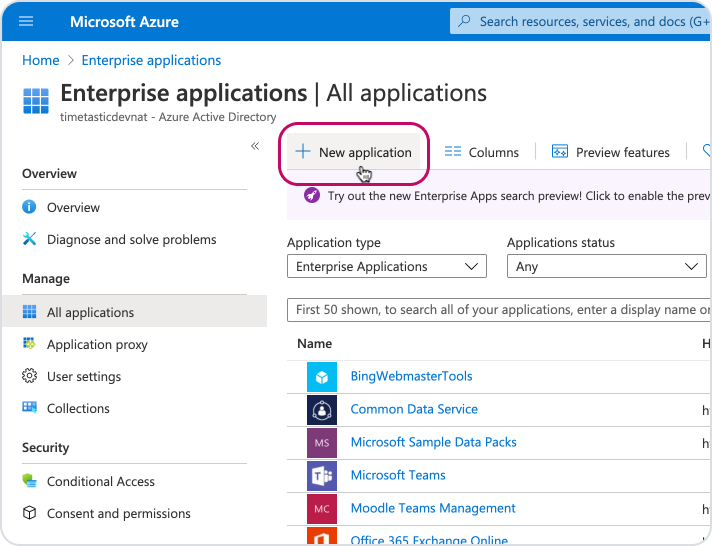
Then 'Create your own application'.
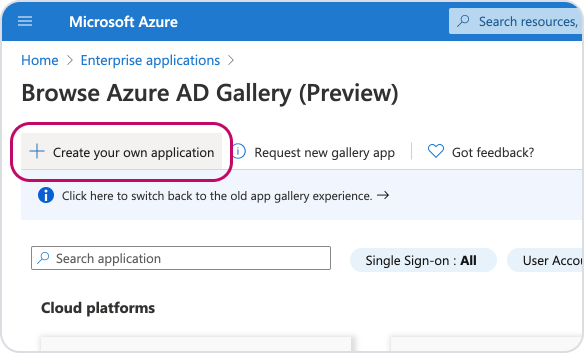
Name your new app 'Timetastic', leave the default setting 'Integrate any other application you don't find in the gallery' and click 'Create'.
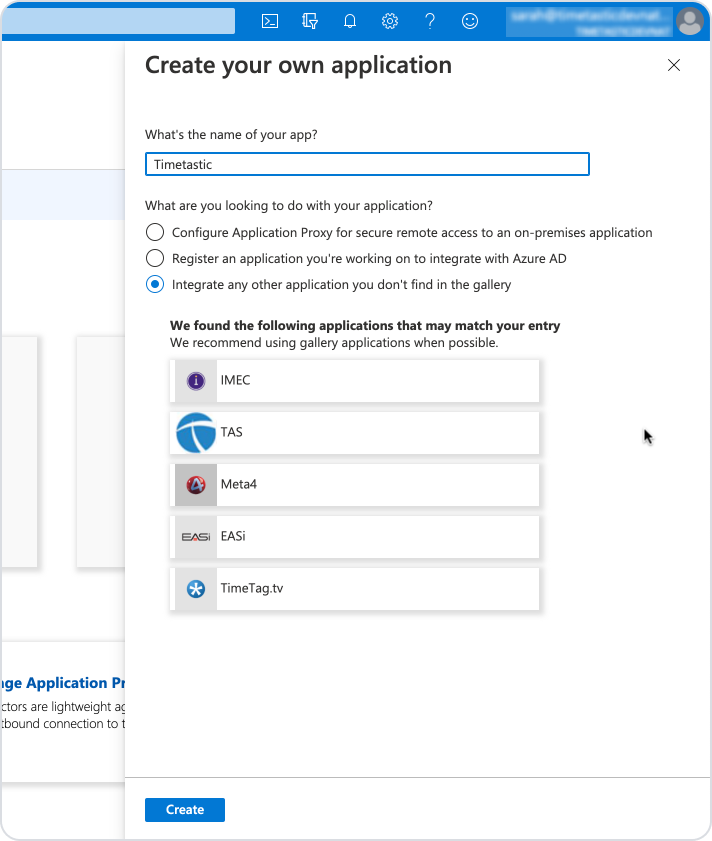
You'll now find yourself in the overview page for your new Timetastic app. Under Getting Started, click the 'Set up single sign on' box.
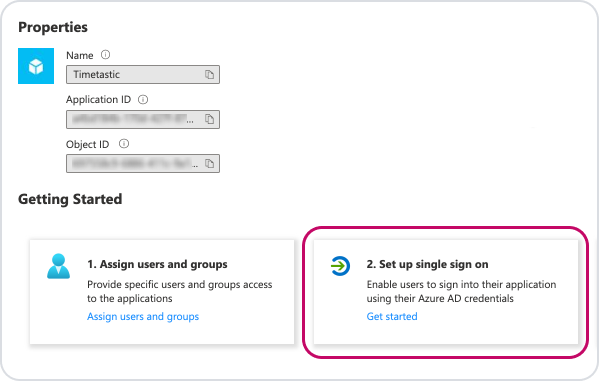
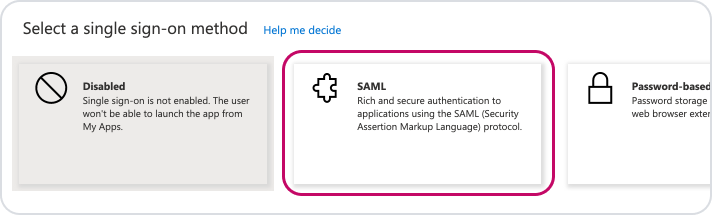
Select 'SAML' as your single sign-on method.
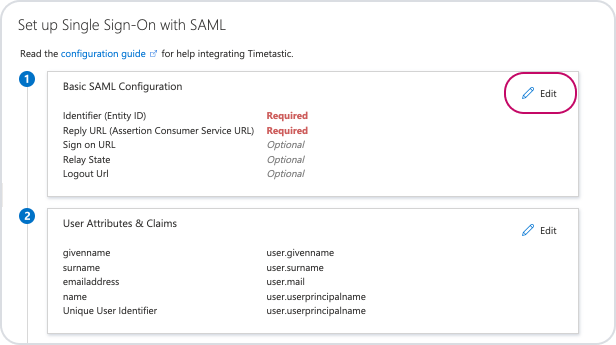
 On this next page, in the 'Basic SAML Configuration' section, click 'Edit'.
On this next page, in the 'Basic SAML Configuration' section, click 'Edit'.
You'll now need to grab some security details from your Timetastic account:
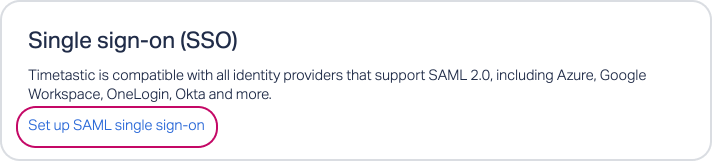
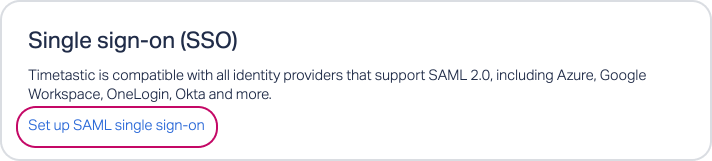
In Timetastic, head to SETTINGS > SECURITY.
Click 'Set up SAML single sign-on'.
Click the 'How to configure your Identity Provider' link to bring up your settings:
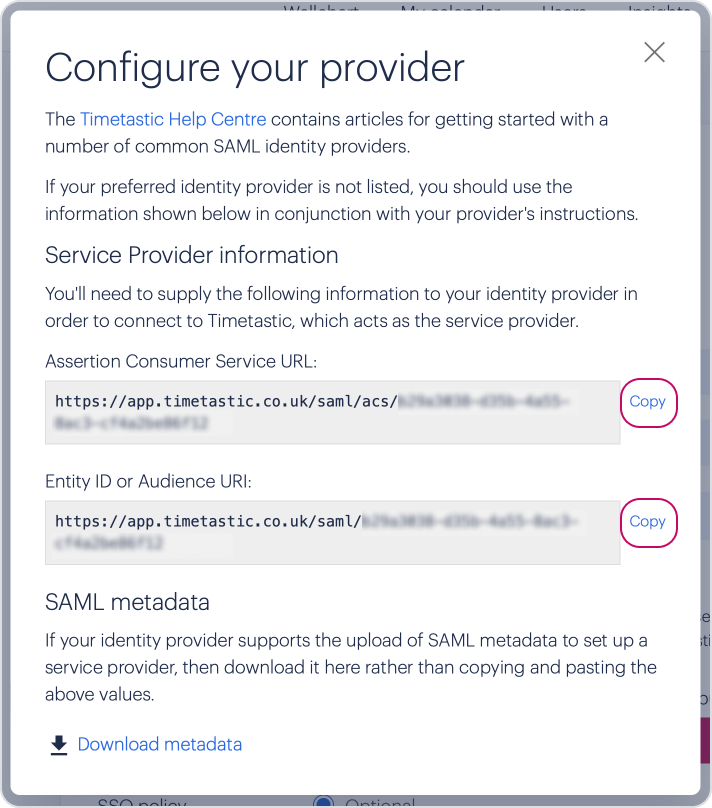
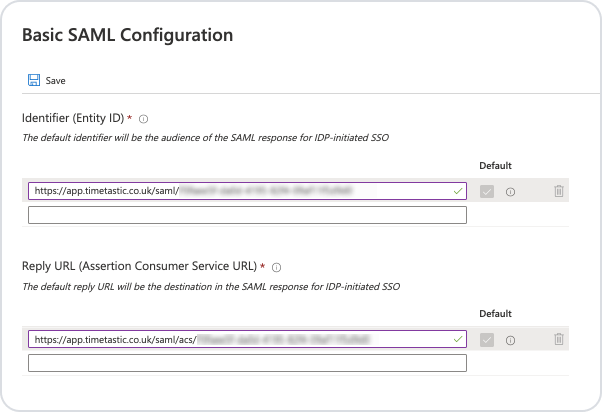
Copy the Assertion Consumer Service URL and paste it into the 'Reply URL (Assertion Consumer Service URL)' field in Azure.
Copy the Entity ID or Audience URI and paste it into the 'Identifier (Entity ID)' field in Azure.
Click 'Save'.
If you're prompted to test SSO with Timetastic, click 'No' as it still won't work at this stage. You need to complete the below steps before you're ready to test.
Granting user access
You'll now need to set which users and groups will be allowed to log in to Timetastic via Azure AD.
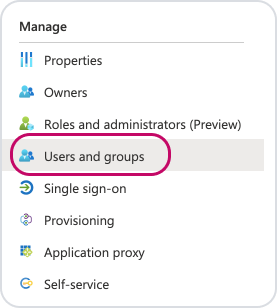
Click on 'Users and groups' on the left hand menu.
Click 'Add User' then select the users/ groups you want to log in to Timetastic via Azure AD.
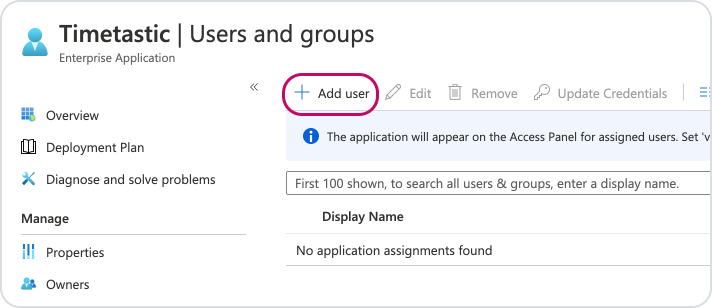
After selecting the relevant users/ groups, click 'Assign'.
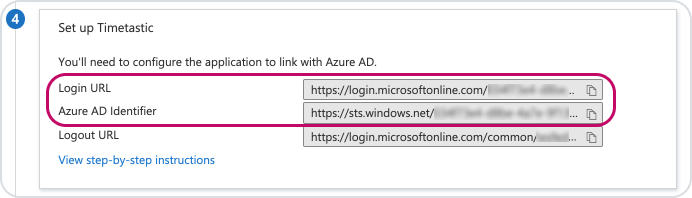
Lastly, before you leave Azure, click back to the 'Single sign on' option on the left hand menu and scroll down to section 4 'Set up Timetastic'. You'll need these details to enter in Timetastic.
Step 2. Timetastic setup
Now it's time to head over to Timetastic. Go to SETTINGS > SECURITY then 'Set up SAML single sign-on'.
In the 'SAML SSO URL' field, paste the 'Login URL' value from Azure.
For 'Issuer entity ID', paste the 'Azure AD Identifier' value from Azure.
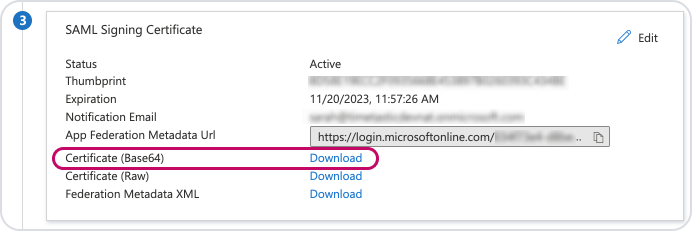
For 'Public certificate', click the 'Download' link next to 'Certificate (Base64)' under section 3 '
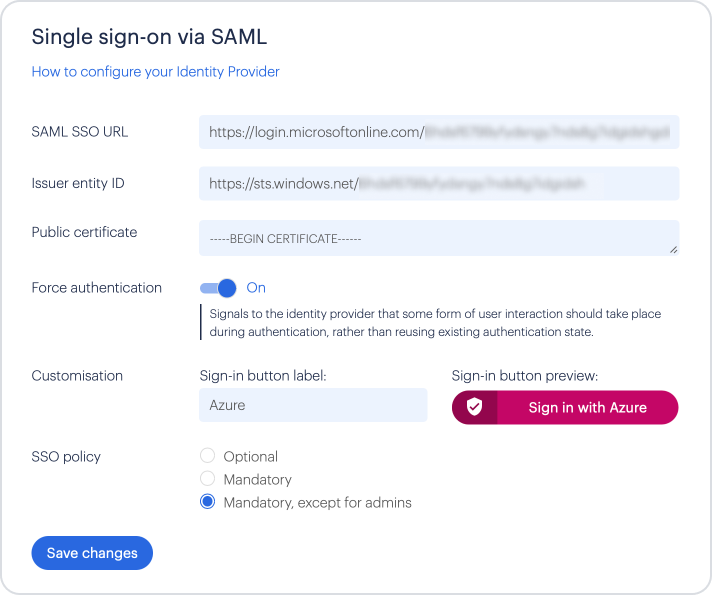
You can turn 'Force authentication' on, if you want users to have to re-enter their identity providers details. (This will only work if the identity providers also support this option)
To customise the Sign-in button, enter something useful, such as 'Azure' against 'Customisation'.
We'd recommend you test SSO is working correctly before making it mandatory.
Once you're happy with your settings, click 'Save changes', then you're good to go!